Installation
![]() The extension can be found on GitHub :
The extension can be found on GitHub :
![]() https://github.com/daggerhart/openid-connect-generic,
https://github.com/daggerhart/openid-connect-generic,
![]() https://github.com/bdegoy/openid-connect-generic (our fork).
https://github.com/bdegoy/openid-connect-generic (our fork).
The plugin installs like any extension, in a classic way or with Composer. See the documentation.
Notes :
![]() The Github source is better maintained than the one of WP website (version tested until 5.1.1 in May 2019).
The Github source is better maintained than the one of WP website (version tested until 5.1.1 in May 2019).
Registering the application on the OAuthSD server
These are steps 1 and 2 of the procedure described here : Link a client application to the OAuthSD server.
Register as an author
By following this procedure you will start by registering as an author on the OAuthSD server.
Register app
You must designate your WordPress application as a client of the OpenID Connect server. To do this, go to the URL : https://oa.dnc.global/web/?page=cre... :
![]() Client Id : Enter a short name, with no spaces or special characters other than ’_’. This is not related to any designation of your application.
Client Id : Enter a short name, with no spaces or special characters other than ’_’. This is not related to any designation of your application.
![]() Secret Client (required) : a short string that can be likened to a strong password. This code must remain secret.
Secret Client (required) : a short string that can be likened to a strong password. This code must remain secret.
![]() Redirect uri (required) : URI back to the client application. If the URL of your WP application is "http: //your_application.ext", enter "http: //your_application.ext/wp-admin/admin-ajax.php ? Action = openid-connect-authorize.
Redirect uri (required) : URI back to the client application. If the URL of your WP application is "http: //your_application.ext", enter "http: //your_application.ext/wp-admin/admin-ajax.php ? Action = openid-connect-authorize.
![]() Grant Type (required) : select "Authorization Code".
Grant Type (required) : select "Authorization Code".
![]() Scopes (required) : Enter "openid profile email".
Scopes (required) : Enter "openid profile email".
WP configuration
This is Step 3 of the procedure.
Go to Settings -> OpenID Connect Client menu.
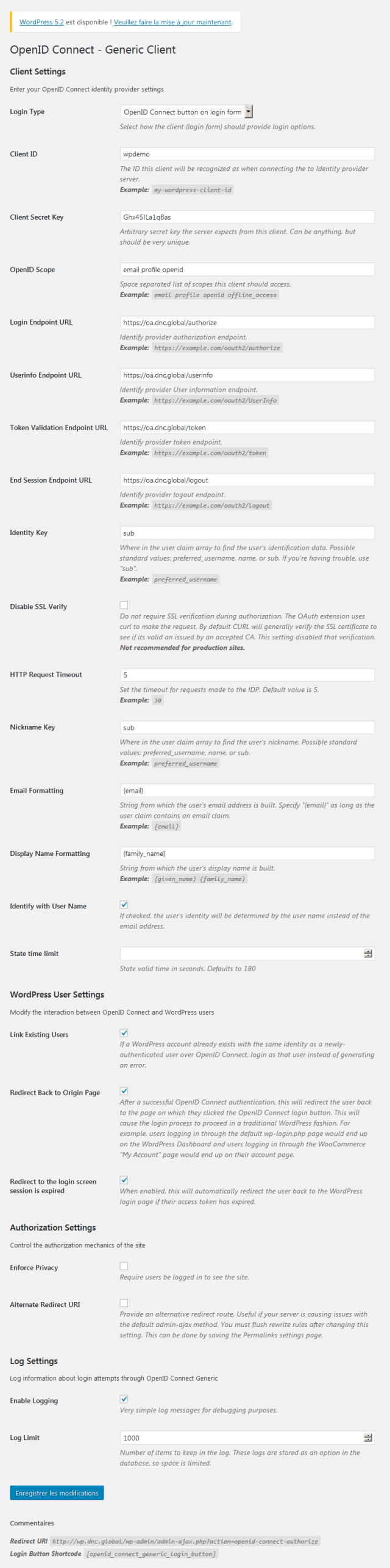
Your Wordpress application must be configured as below, where Client ID and Client Secret Key are the values listed previously on the server :
Registering an user on OAuthSD
The principle of Single Sign On (SSO) allows a user to connect to different applications with the same identifiers (login, password ...).
You must first register a user on OAuthSD (or use an existing OAuthSD user). Doing the opposite (creating the user on your WP application and registering it on the OpenID Connect server) would go against the principle.
The registration of a user is done here : https://oa.dnc.global/web/spip.php?...
User created by WP
If the user does not exist on the WP side, the extension will create it.
Notes :
![]() If one tries to log in with an OIDC user ID that already exists for a WP user, the plugin creates a WP user with an incremented identifier ; for example if the login is "admin", the user WP of identifier "admin2" will be created with a "subscriber" role. It will be up to the WP site administrator to possibly modify this role.
If one tries to log in with an OIDC user ID that already exists for a WP user, the plugin creates a WP user with an incremented identifier ; for example if the login is "admin", the user WP of identifier "admin2" will be created with a "subscriber" role. It will be up to the WP site administrator to possibly modify this role.
![]() If the OpenID user email already exists for a different WP user, OpenID is the master : the most logical thing will be to change this WP user’s ID to the OpenID user’s ID (since the email unambiguously designates a person ).
If the OpenID user email already exists for a different WP user, OpenID is the master : the most logical thing will be to change this WP user’s ID to the OpenID user’s ID (since the email unambiguously designates a person ).
Errors from Setup
![]() Missing state - Most of the time, this error comes from the fact that the user has been too long to log in, or has returned to an old form. Just start over.
Missing state - Most of the time, this error comes from the fact that the user has been too long to log in, or has returned to an old form. Just start over.
![]() User claim incomplete - Occurs when the list of declarations (claims) returned by Userinfo, based on scopes defined for the application does not contain those defined in the format.
User claim incomplete - Occurs when the list of declarations (claims) returned by Userinfo, based on scopes defined for the application does not contain those defined in the format.
For example :
- the application has been configured without the scope email (OpenID Scope configuration field) and the format Email Formatting is email.
- Display Name Formatting was set to name while this field is null in the OpenID server for the user in question and the user name is in the family_name declaration.
![]() Failed user creation - Occurs most often when WP is trying to create a new user and the e-mail declared by the OIDC user already exists on the WP side.
Failed user creation - Occurs most often when WP is trying to create a new user and the e-mail declared by the OIDC user already exists on the WP side.
![]() redirect_uri_mismatch : The redirect URI provided is missing or does not match - This error is generated by the OAuthSD server in response to the request to the Authorize controller. It occurs when the Redirect URI registered on the OAuthSD server does not conform to the bottom of the Settings -> OpenID Connect - Generic Client form. In particular, OAuthSD requires secured transfer protocol (https).
redirect_uri_mismatch : The redirect URI provided is missing or does not match - This error is generated by the OAuthSD server in response to the request to the Authorize controller. It occurs when the Redirect URI registered on the OAuthSD server does not conform to the bottom of the Settings -> OpenID Connect - Generic Client form. In particular, OAuthSD requires secured transfer protocol (https).
Demonstration
https://wp.dnc.global/2019/05/11/ex... is a demonstrator of a WP application linked to OAuthSD with this extension.
Monitoring : development in progress
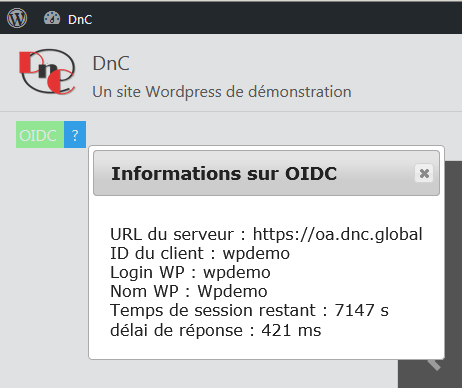 We are developing a fork that includes monitoring.
We are developing a fork that includes monitoring.
![]() The code is visible here : https://github.com/bdegoy/openid-co....Operation is similar to what has been described for Plugin OpenID Connect Client pour SPIP.
The code is visible here : https://github.com/bdegoy/openid-co....Operation is similar to what has been described for Plugin OpenID Connect Client pour SPIP.


