What is 2FA ?
Two Factor Authentication, also known as 2FA, two step verification or TFA (as an acronym), is an extra layer of security that is known as “multi factor authentication” that requires not only a password and username but also something that the user owns, that is with them and that no one else owns or knows about.
After login, give a second proof
The process begins as usual, the end-user giving his login and password :
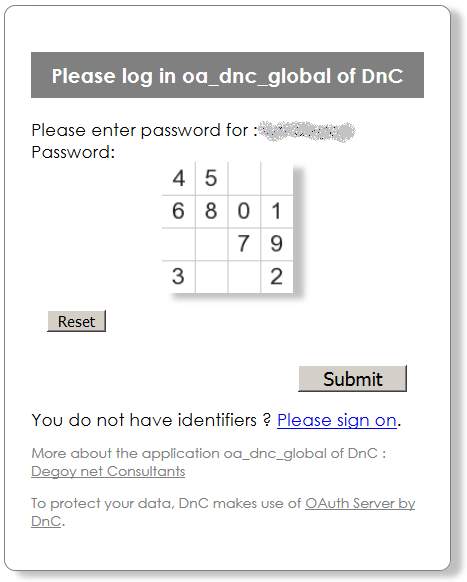
She/he is asked to provide a second proof of identity : OAuthSD offers the classic method : SMS or Google Authenticator. We add our own highly securised identification system : DnC’s IdentMaster.
2FA by SMS
If this first step ends successfully, OAuthSD continues on a request for code by SMS :
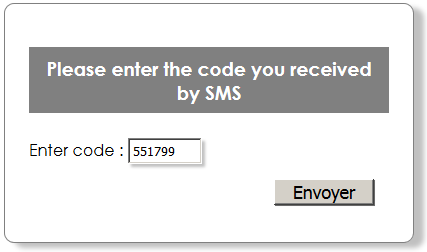
The SMS is sent to the smartphone number registered with the user’s profile [1].
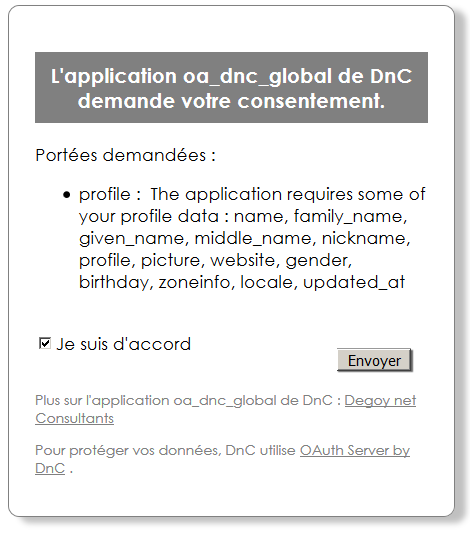
After confirmation, consent is requested if necessary, as usual :
2FA with Google Authenticator
Google Authenticator is a 2FA system that generates a TOTP.
What is TOTP ?
TOTP is a short form for Time-based One-time Password (usually called Token) which is password that can only be used once and is only valid to be used in a defined time range. Usually TOTP generators generate new passwords every defined tens of seconds.
This necessitates to register OAuthSD as a Google Authenticator application [2]. This is what the QRCode is used for. See many how-to on the Web. This is a one-time action for the smartphone life time : once it is done, GA will display a code every 30s : nothing to remember !
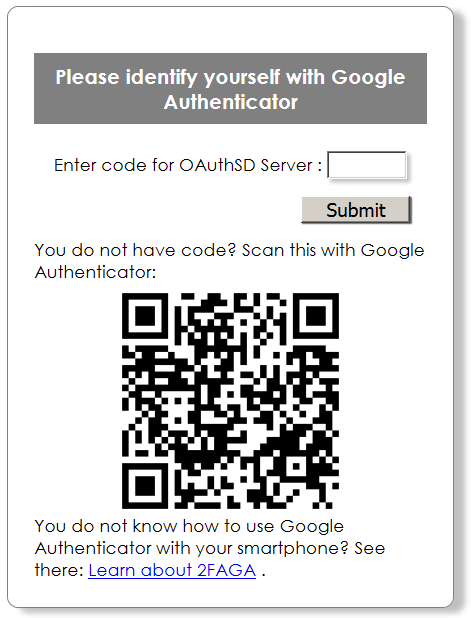
After confirmation, Consent is asked if necessary, as usual.
Why Google Authenticator ?
Google Authenticator has been provided by Google for several years and proved a user-friendly process. Many people have Google Authenticator (for free) on their smartphone, and would probably have difficulties adopting an other application.
What about tracking ? Applications delegate user identification to OAuthSD, this means Google see the OAuthSD server, not the applications. Google knows that a user is related to OAuthSD, but doesn’t see the relation with the application ... provided there is no tracking leakage elsewhere in this application !
TFA with DnC’s IdentMaster
We have developped DnC’s IdentMaster, a passwordless mobile application that can be used as first as well as second authentication method.
With the DnC’s IdentMaster application installed on your mobile, you just need to scan the QR-Code presented by the application to open your OpenID Connect session :
Configure 2FA on OAuthSD
A request for a second validation is presented to the end user :
![]() if the reserved scope "tfa" is present in the authorization request and if the application has been registered on the server with the scope ’tfa’.
if the reserved scope "tfa" is present in the authorization request and if the application has been registered on the server with the scope ’tfa’.
![]() If the LOGIN_WITH_TFA configuration constant is set to true, the 2FA form will always be presented to the end user after the login form.
If the LOGIN_WITH_TFA configuration constant is set to true, the 2FA form will always be presented to the end user after the login form.
![]() the TFA_PROVIDER configuration constant is used to define the second mode of identification ("gangsta", "checkbysms ", " smartconnect "...).
the TFA_PROVIDER configuration constant is used to define the second mode of identification ("gangsta", "checkbysms ", " smartconnect "...).
And then ?
In the current state of development, OAuthSD offers three methods for 2FA : TFA by SMS (the classic solution !), Google Authenticator and SmatConnect.
Other ID providers will follow soon, including our own (= your private) for a top level security.
We may develop any private system suited for the particular needs of our customers, as we did with the OpenID Connect Identification with ID Card : Aramis .


